
Australia’s digital landscape is under relentless assault. In 2023 alone, major data breaches at Optus and Medibank compromised the personal information of millions of Australians, highlighting the ever-present vulnerability of our digital infrastructure. The Australian Cyber Security Centre (ACSC) reported a concerning 13% year-on-year increase in cybercrime reports during 2022-23, translating to a cyber attack occurring roughly every seven minutes. This translates to a constant barrage on Australian businesses, bombarding their digital perimeters with a relentless stream of threats.
Cybersecurity is no longer a luxury; it’s a fundamental business imperative. Businesses of all sizes hold valuable data – customer records, financial information, intellectual property – and a successful cyberattack can be devastating. The ramifications can include operational disruption, crippling downtime, and a significant erosion of customer trust. In the wake of a high-profile attack, businesses can also face hefty financial penalties for failing to adequately safeguard sensitive data.
Traditional security solutions, like firewalls and antivirus software, have long been the first line of defence. However, the sophistication and relentlessness of cybercriminals necessitate a more proactive approach. Managed Detection and Response (MDR) services offer a comprehensive solution, providing continuous monitoring, advanced threat detection, and rapid incident response. This article delves into the critical role of MDR in enhancing 24/7 threat monitoring and incident response capabilities, empowering Australian businesses to stay ahead of cyber threats and protect their valuable assets.
Traditional Security Limitations

For years, Australian businesses have relied on a traditional security arsenal to safeguard their digital perimeters. These solutions act as the initial line of defence, employing various tools to deter and identify threats. Firewalls function as meticulous gatekeepers, rigorously inspecting incoming and outgoing network traffic, permitting only authorized exchanges. Antivirus software acts as a vigilant shield, constantly scanning for and neutralizing malicious code known to compromise devices. Intrusion Detection Systems (IDS) actively monitor network activity for suspicious patterns, attempting to flag potential breaches in real-time.
While these solutions offer a valuable security layer, their limitations become increasingly apparent in today’s dynamic cyber threat landscape. A critical shortcoming of traditional security lies in its reactive approach. It excels at identifying and blocking pre-defined threats but struggles to adapt to the ever-evolving tactics of cybercriminals. Emerging malware, zero-day exploits, and sophisticated social engineering schemes can often bypass these defences undetected.
The 24/7 vigilance required for effective threat monitoring can also be a significant challenge with traditional security solutions. In-house IT teams tasked with managing these tools require ongoing training to maintain and update a multitude of software programs. This translates to a substantial time and resource commitment, potentially hindering the ability to maintain consistent 24/7 monitoring, especially for smaller businesses with limited IT staff.
Furthermore, traditional security solutions may lack the advanced threat detection capabilities needed to identify nuanced attacks. While they excel at flagging known malicious signatures, they often struggle to detect novel threats or those cleverly disguised as legitimate activity. This limited visibility into sophisticated cyberattacks can leave businesses vulnerable during critical off-hours when traditional monitoring may be less stringent.
| Security Solution | Functionality |
|---|---|
| Firewall | Controls incoming and outgoing network traffic |
| Antivirus Software | Scans for and neutralizes malicious code |
| Intrusion Detection System (IDS) | Monitors network activity for suspicious patterns |
| Data Loss Prevention (DLP) | Prevents sensitive data from unauthorized disclosure |
MDR Services Explained
Managed Detection and Response (MDR) services offer a paradigm shift in cybersecurity, transforming reactive threat defence into a proactive approach. MDR acts as a virtual extension of an organization’s security team, providing continuous monitoring, advanced threat detection, and rapid incident response capabilities all crucial aspects for effective 24/7 threat management.
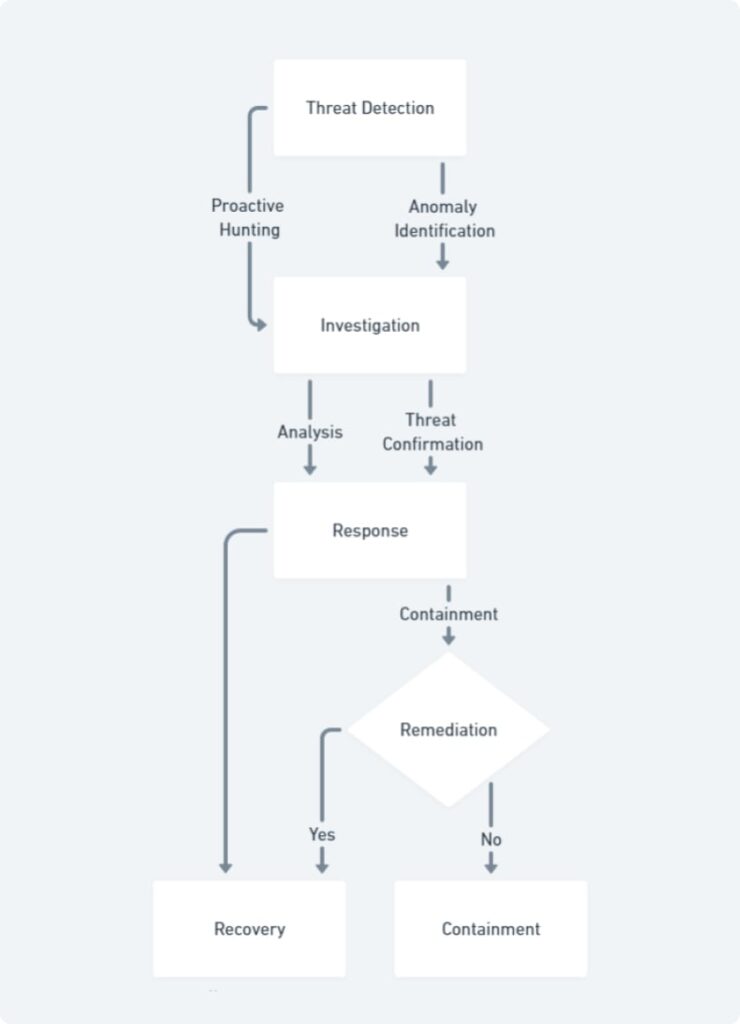
At the core of MDR lies its proactive threat hunting methodology. Unlike traditional security solutions that wait for threats to emerge, MDR services actively seek out hidden vulnerabilities and suspicious activity within an organization’s network. Security specialists leverage advanced tools like machine learning (ML) and threat intelligence feeds to identify subtle anomalies and patterns that might evade traditional signature-based detection. This proactive approach allows MDR providers to neutralize threats before they can inflict significant damage, significantly reducing the potential for costly downtime and data breaches.
The cornerstone of effective 24/7 threat monitoring is continuous vigilance. MDR services address this challenge by employing dedicated Security Operations Centers (SOCs) staffed by security experts with extensive experience in threat detection and incident response. These professionals operate around the clock, meticulously analyzing security logs and network activity for signs of malicious activity, even outside regular business hours. This ensures that an organization’s security posture remains vigilant, even during periods when internal IT resources may be limited.
When a potential threat is detected, rapid response is critical to minimize potential damage. MDR services excel in this area, employing well-defined incident response processes. Upon detection, MDR providers initiate containment measures to isolate the threat, preventing it from further compromising the network. A thorough investigation follows to determine the scope and impact of the threat. Finally, MDR teams implement remediation actions to neutralize the threat and restore normalcy to the affected systems. This rapid response capability, facilitated by 24/7 monitoring and dedicated security expertise, significantly reduces the window of opportunity for cybercriminals to exploit vulnerabilities.
Benefits of MDR for 24/7 Threat Management

In the relentless battle against cyber threats, MDR services offer Australian businesses a significant advantage: enhanced 24/7 threat management capabilities. Here’s how MDR empowers organizations to stay ahead of cybercriminals:
Superior Threat Detection and Prevention: MDR goes beyond signature-based detection, leveraging advanced threat intelligence and machine learning algorithms. This allows for the identification of novel and evolving threats before they can wreak havoc. By proactively hunting for vulnerabilities and suspicious activity, MDR providers can neutralize threats in their early stages, minimizing potential damage to critical systems and data.
Faster Response Times, Reduced Downtime: The ever-present risk of cyberattacks necessitates a rapid response to minimize disruption. MDR services address this challenge with dedicated security teams operating around the clock. Upon detecting a potential threat, these experts can initiate a swift incident response process, containing the threat, investigating its scope, and implementing remediation measures. This swift action minimizes the window of opportunity for cybercriminals and reduces the potential for costly downtime.
Enhanced Visibility and Threat Identification: Traditional security solutions often lack the comprehensive view of network activity needed for effective threat detection. MDR services, however, provide extensive visibility into an organization’s network. Security specialists can analyze vast amounts of data from various sources, identifying subtle anomalies and patterns that might otherwise go unnoticed. This enhanced visibility empowers MDR providers to proactively identify and contain threats before they escalate into major security incidents.
Beyond the technical benefits, MDR offers a compelling value proposition from a cost-effectiveness standpoint. Building and maintaining a robust in-house Security Operations Center (SOC) capable of 24/7 monitoring requires significant investment in personnel, technology, and ongoing training. MDR offers a cost-effective alternative, providing access to advanced security expertise and technology at a predictable subscription fee. This makes MDR an attractive option for businesses of all sizes, particularly those with limited internal security resources.
The Australian cyber threat landscape is a dynamic battleground, demanding constant vigilance and proactive security measures. Traditional security solutions, while valuable, struggle to keep pace with the ever-evolving tactics of cybercriminals. MDR services offer a powerful solution, transforming threat defence from a reactive approach to a proactive one. By leveraging 24/7 monitoring, advanced threat detection, and rapid incident response, MDR empowers Australian businesses to stay ahead of cyber threats and safeguard their critical assets. As the sophistication of cyberattacks continues to rise, MDR stands as a vital tool for organizations to fortify their digital defenses and ensure a secure future.
