
The landscape of work in Australia is undergoing a significant transformation, characterised by the increasing prevalence of remote and distributed workforces. This shift, accelerated by technological advancements and the global pandemic, has necessitated a re-evaluation of traditional workplace security measures. Identity and Access Management (IAM) emerges as a critical component in this new paradigm, ensuring that organisations can maintain secure collaboration among geographically dispersed teams.
IAM systems play a pivotal role in safeguarding sensitive data and managing user access across diverse locations. With over 40% of Australian employees engaging in remote work in 2023, the risk of security breaches has amplified considerably. The Australian Cyber Security Centre (ACSC) reported a 13% increase in cybercrime incidents, underscoring the urgent need for robust IAM solutions. These systems not only authenticate and authorise users but also provide detailed oversight, ensuring that only authorised personnel can access critical information.
Secure collaboration is essential for modern businesses as it fosters trust, efficiency, and compliance. In an era where data breaches can lead to severe financial and reputational damage, implementing effective IAM practices is paramount. By leveraging IAM, organisations can enhance their security posture, enabling seamless and secure interactions within a distributed workforce.
The Evolution of Work in Australia

Historical Perspective
The traditional office setup in Australia, characterised by centralised workplaces and fixed working hours, has undergone a profound transformation over recent decades. Initially driven by technological advancements, this shift gained unprecedented momentum during the COVID-19 pandemic, which necessitated remote work on an unprecedented scale. Companies were compelled to adopt flexible working arrangements to maintain business continuity, leading to a permanent change in the workplace paradigm.
Current Trends
Today, the Australian workforce is marked by a blend of remote, in-office, and hybrid work models. Remote work, once considered a perk, has become a standard practice for many organisations. Hybrid models, combining remote and on-site work, have emerged as a popular choice, offering employees greater flexibility while maintaining essential in-person interactions. This trend reflects a broader recognition of the benefits of work-life balance and employee well-being.
Statistics and Data
The adoption of remote work in Australia is substantiated by compelling statistics. According to the Australian Bureau of Statistics (ABS), as of 2023, approximately 45% of employed Australians regularly work from home. This represents a significant increase from pre-pandemic levels, where less than 20% engaged in remote work. Additionally, a survey by Deloitte found that 78% of Australian businesses plan to retain flexible work arrangements post-pandemic.
| Year | Percentage of Remote Workers |
|---|---|
| 2019 | 18% |
| 2020 | 35% |
| 2023 | 45% |
This shift underscores the importance of implementing robust systems, such as IAM, to manage the complexities of a distributed workforce. IAM solutions are essential for ensuring that employees can access necessary resources securely, regardless of their location, thus facilitating the ongoing evolution of work in Australia.
Understanding Identity and Access Management (IAM)
Definition
Identity and Access Management (IAM) is a framework of policies and technologies designed to ensure that the right individuals have appropriate access to organisational resources. It encompasses a range of processes and tools used to identify, authenticate, and authorise users, granting or restricting their access to specific systems and data. The core components of IAM include user identity management, access control, and directory services.
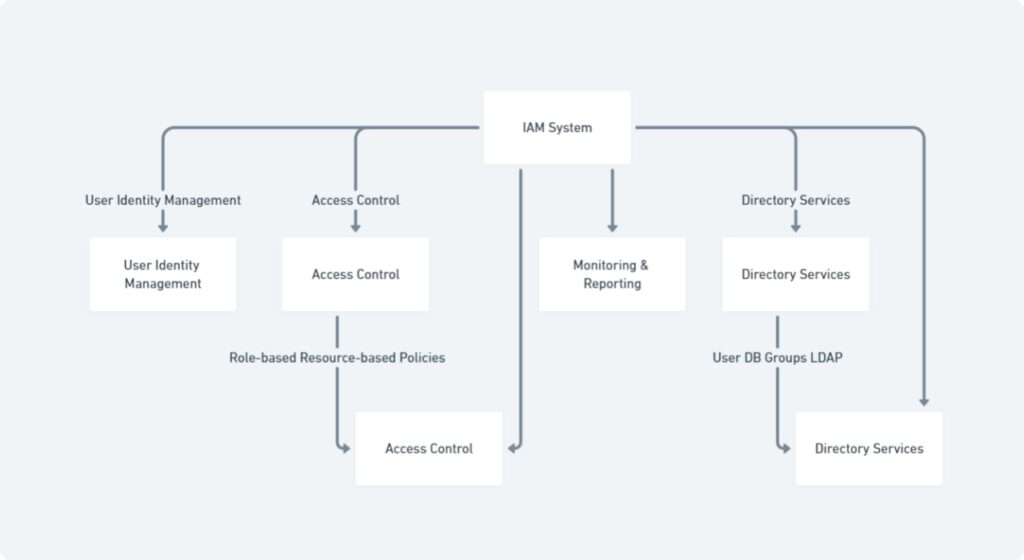
Key Functions
The primary functions of IAM are critical to maintaining organisational security and operational efficiency. Authentication is the process of verifying a user’s identity, typically through credentials such as passwords, biometrics, or multi-factor authentication methods. Authorisation determines what an authenticated user is permitted to do, ensuring they have access only to the resources necessary for their role. User management involves the administration of user identities throughout their lifecycle, including provisioning new accounts, managing permissions, and deactivating accounts when they are no longer required.
| Function | Benefits |
|---|---|
| Authentication | Improves security |
| Authorization | Ensures appropriate access |
| User Management | Enhances operational efficiency |
| Auditing | Detects potential security threats |
| Reporting | Compliance with regulations |
IAM systems also provide auditing and reporting capabilities, enabling organisations to monitor access patterns and detect potential security threats. By implementing robust IAM practices, organisations can safeguard sensitive information, comply with regulatory requirements, and enhance the overall security posture, particularly in environments with distributed or remote workforces.
The Role of IAM in Enabling Secure Collaboration

Security Challenges
Distributed workforces present unique security challenges for organisations. As employees access corporate resources from various locations and devices, the risk of unauthorised access and data breaches increases significantly. The proliferation of endpoints, such as laptops, smartphones, and tablets, complicates the management of user identities and access rights. Additionally, the use of unsecured networks and personal devices heightens the vulnerability to cyber-attacks and unauthorised data access. Ensuring that only legitimate users can access sensitive information becomes a paramount concern.
IAM Solutions
Identity and Access Management (IAM) solutions address these security challenges by providing a structured and secure approach to managing user identities and access rights. Through robust authentication mechanisms, IAM systems verify the identity of users before granting access to corporate resources. Multi-factor authentication (MFA) adds an additional layer of security by requiring multiple forms of verification, thereby reducing the risk of unauthorised access. Authorisation processes ensure that users have access only to the resources necessary for their specific roles, minimising the potential for data exposure.
IAM solutions also include comprehensive user management capabilities, which streamline the provisioning and de-provisioning of user accounts. Automated workflows ensure that employees have the appropriate access from their first day of work and that access is promptly revoked when no longer needed. Additionally, IAM systems offer auditing and reporting features, enabling organisations to monitor access patterns and detect any anomalies or potential security threats. This proactive approach helps in maintaining a secure and compliant environment for distributed workforces.
Case Studies
Several Australian companies have successfully implemented IAM solutions to enhance secure collaboration within their distributed workforces. For instance, Atlassian, a leading software company, uses IAM to manage access to its internal and customer-facing applications. By integrating MFA and automated user provisioning, Atlassian has significantly reduced the risk of unauthorised access and streamlined its access management processes.
Another example is Telstra, Australia’s largest telecommunications company, which employs IAM to secure its extensive network of remote employees. By leveraging IAM solutions, Telstra ensures that its workforce can securely access corporate resources, regardless of their location, thereby enhancing both productivity and security.
These case studies demonstrate the critical role of IAM in enabling secure collaboration and protecting sensitive data in distributed work environments. For further details, refer to the relevant case studies and articles on IAM implementations in Australian companies.
Future Work Trends and IAM
Technological Advancements

The future of work is being shaped by rapid technological advancements, particularly in artificial intelligence (AI), machine learning, and the Internet of Things (IoT). AI and machine learning are transforming business processes, enabling predictive analytics, automation, and enhanced decision-making. IoT is expanding the network of connected devices, from smart office equipment to wearables, further integrating technology into everyday work environments. These innovations are driving efficiencies and creating new opportunities for remote and hybrid work models.
IAM Adaptation
To keep pace with these technological trends, Identity and Access Management (IAM) systems must evolve. The integration of AI and machine learning into IAM can enhance security through adaptive authentication, which dynamically adjusts security measures based on user behaviour and risk factors. Additionally, IAM systems need to support a growing number of IoT devices, ensuring secure and seamless access to corporate networks. This includes implementing granular access controls and real-time monitoring to manage the diverse and expanding array of endpoints.
Predictions
Looking ahead, IAM will become increasingly sophisticated and integral to the secure management of distributed workforces. Predictive analytics will play a crucial role in identifying potential security threats before they materialise, allowing organisations to respond proactively. The adoption of decentralised identity management, leveraging blockchain technology, is likely to gain traction, providing greater security and privacy for users. Furthermore, as remote and hybrid work models become the norm, IAM systems will need to offer enhanced flexibility and scalability to accommodate varying access needs and emerging technologies.
In summary, the future of work will be defined by technological advancements that necessitate the continual adaptation of IAM systems. By embracing these changes, organisations can ensure secure collaboration and maintain a competitive edge in the evolving workplace landscape.
Implementation of IAM in Australian Businesses
Best Practices
Implementing Identity and Access Management (IAM) in Australian businesses requires adherence to best practices to ensure effective security and operational efficiency. Firstly, a thorough assessment of the current IT environment is essential to identify potential vulnerabilities and define IAM requirements. Businesses should adopt multi-factor authentication (MFA) to enhance security, combining something the user knows (password) with something the user has (security token) or something the user is (biometric data).
Role-based access control (RBAC) is another critical practice, assigning permissions based on users’ roles within the organisation, thereby minimising unnecessary access to sensitive information. Regular audits and reviews of access permissions are vital to maintain up-to-date and secure access controls. Additionally, automated provisioning and de-provisioning of user accounts can streamline the onboarding and offboarding processes, reducing the risk of orphaned accounts and potential security breaches.
Compliance
In Australia, businesses must comply with various regulations and standards related to IAM. The Australian Privacy Act 1988 mandates the protection of personal information, requiring organisations to implement robust security measures, including IAM systems, to safeguard data. Furthermore, the Notifiable Data Breaches (NDB) scheme under the Privacy Act compels businesses to notify affected individuals and the Office of the Australian Information Commissioner (OAIC) of data breaches involving personal information.
The Australian Cyber Security Centre (ACSC) also provides guidelines and best practices for IAM implementation, which align with international standards such as ISO/IEC 27001 for Information Security Management. Adhering to these regulations and guidelines not only ensures compliance but also enhances the overall security posture of Australian businesses.
For more detailed information on compliance requirements, refer to the OAIC guidelines and ACSC recommendations.
By following these best practices and compliance requirements, Australian businesses can effectively implement IAM systems, ensuring secure access management and protection of sensitive information.
In summary, the evolution of work in Australia towards remote and distributed models necessitates robust Identity and Access Management (IAM) systems. IAM ensures secure collaboration by addressing the unique security challenges of a dispersed workforce through authentication, authorisation, and comprehensive user management. As future work trends, driven by technological advancements, continue to emerge, IAM systems must adapt to maintain security and efficiency. The implementation of best practices and compliance with Australian regulations further strengthens this security framework. Ultimately, IAM is indispensable for safeguarding sensitive information and enabling secure, efficient collaboration in the evolving landscape of work.
