
Identity and Access Management (IAM) has become an essential pillar in the cybersecurity framework of Australian businesses. As cyber threats continue to evolve in both sophistication and frequency, the need for robust IAM systems has never been more critical. A 2023 report by the Australian Cyber Security Centre revealed a 13% increase in cyber incidents, underscoring the pressing need for stringent access controls and identity verification mechanisms. IAM not only helps in safeguarding sensitive data but also ensures compliance with national regulations such as the Privacy Act 1988 and the Notifiable Data Breaches (NDB) scheme. By implementing effective IAM strategies, businesses can mitigate risks associated with unauthorised access and enhance their overall security posture. Furthermore, IAM supports operational efficiency by streamlining user access across various systems, thereby reducing administrative burdens and fostering a secure, seamless user experience.
What is IAM?
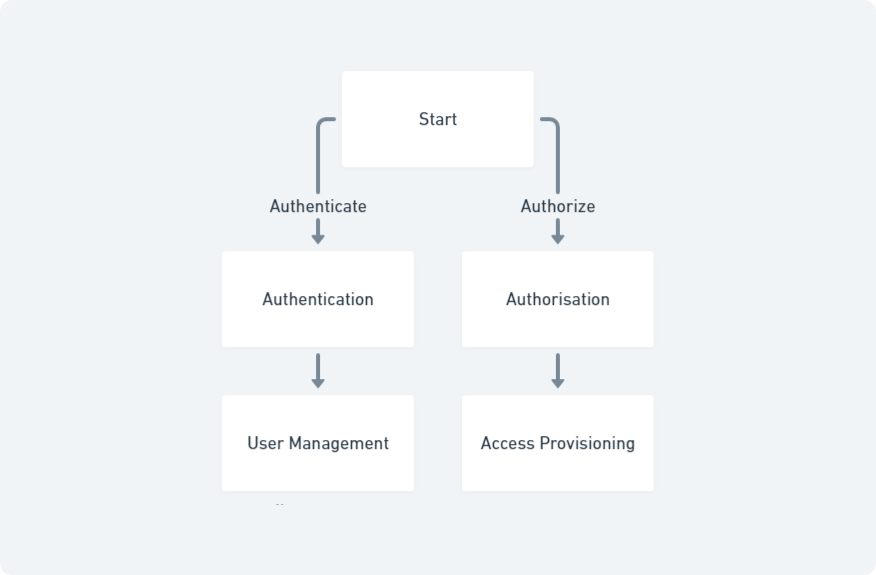
Identity and Access Management (IAM) is a comprehensive framework used to manage digital identities and control access to information systems. At its core, IAM encompasses several critical components: authentication, authorisation, and user management. Authentication verifies the identity of users attempting to access a system, typically through methods such as passwords, biometrics, or multi-factor authentication (MFA). Authorisation determines the level of access granted to authenticated users, ensuring they can only interact with resources pertinent to their roles.
User management involves the creation, maintenance, and deletion of user accounts, alongside the management of user roles and permissions. This component ensures that only authorised personnel have access to sensitive data, which is vital for maintaining security and compliance.
IAM integrates seamlessly into IT infrastructure, acting as a gatekeeper between users and critical resources. It supports various protocols and standards, such as LDAP, SAML, and OAuth, to facilitate secure communication and interoperability between different systems and applications. By implementing IAM, organisations can ensure that access rights are enforced consistently across all platforms, reducing the risk of data breaches and unauthorised access.
Reputable cybersecurity sources, such as the National Institute of Standards and Technology (NIST), define IAM as a strategic initiative essential for protecting organisational assets and ensuring regulatory compliance. A basic flowchart illustrating the IAM process typically starts with user authentication, followed by authorisation, and culminates in access provisioning, thereby providing a clear visual representation of how IAM functions within an enterprise environment.
The Importance of IAM in Australia

Identity and Access Management (IAM) is crucial for Australian businesses due to the growing cybersecurity threats and stringent regulatory requirements. The Australian Cyber Security Centre (ACSC) reports a significant rise in cyber incidents, with a 13% increase in 2023, emphasising the need for robust IAM systems to protect sensitive information.
Regulations such as the Privacy Act 1988 and the Notifiable Data Breaches (NDB) scheme necessitate stringent data protection measures. IAM aids in compliance by ensuring only authorised individuals can access critical data and systems. The ACSC guidelines provide comprehensive recommendations for implementing effective IAM strategies, highlighting the importance of authentication, authorisation, and user management.
Implementing IAM enhances security through multi-factor authentication (MFA), streamlines user access management, and reduces the risk of data breaches. By centralising identity management, organisations can monitor and control user activities efficiently, ensuring access permissions are appropriate and up-to-date. Additionally, IAM supports operational efficiency by automating user provisioning and de-provisioning processes, thus reducing administrative overhead.
For further information on IAM best practices and regulatory requirements, refer to the ACSC guidelines.
Key IAM Components
Identity and Access Management (IAM) systems comprise several critical components that collectively ensure secure and efficient access to resources. These components include single sign-on (SSO), multi-factor authentication (MFA), user provisioning, and access governance.
Single Sign-On (SSO)
SSO permits users to access various applications using a single set of credentials. This streamlines the user experience and mitigates the risk of password fatigue. Technologies like Okta and Microsoft Azure AD provide robust SSO solutions, enabling seamless access to a variety of applications and services.
Multi-Factor Authentication (MFA)
MFA enhances security by requiring multiple forms of verification before granting access. This may encompass something the user knows (password), something the user possesses (security token), or something inherent to the user (biometric verification). Microsoft Azure AD and Google Authenticator are popular tools that offer MFA capabilities, significantly reducing the likelihood of unauthorised access.
User Provisioning
User provisioning automates the creation, management, and deletion of user accounts. This process ensures that users have appropriate access rights based on their roles within the organisation. IAM tools like SailPoint and Okta facilitate efficient user provisioning, ensuring that access permissions are promptly updated as roles change.
Access Governance
Access governance involves monitoring and managing user access to ensure compliance with policies and regulations. It includes processes like access reviews, role management, and audit reporting. Tools such as IBM Security Identity Governance and SailPoint IdentityIQ provide comprehensive access governance features, helping organisations maintain compliance and minimise security risks.
| Feature | Okta | Microsoft Azure AD | SailPoint IdentityIQ | IBM Security Identity Governance |
|---|---|---|---|---|
| SSO | Yes | Yes | No | No |
| MFA | Yes | Yes | Yes | Yes |
| User Provisioning | Yes | Yes | Yes | Yes |
| Access Governance | Basic | Basic | Advanced | Advanced |
This table highlights the key features of popular IAM tools, illustrating their capabilities in SSO, MFA, user provisioning, and access governance. By leveraging these tools, organisations can enhance their security posture and streamline access management processes.
IAM Implementation Strategies
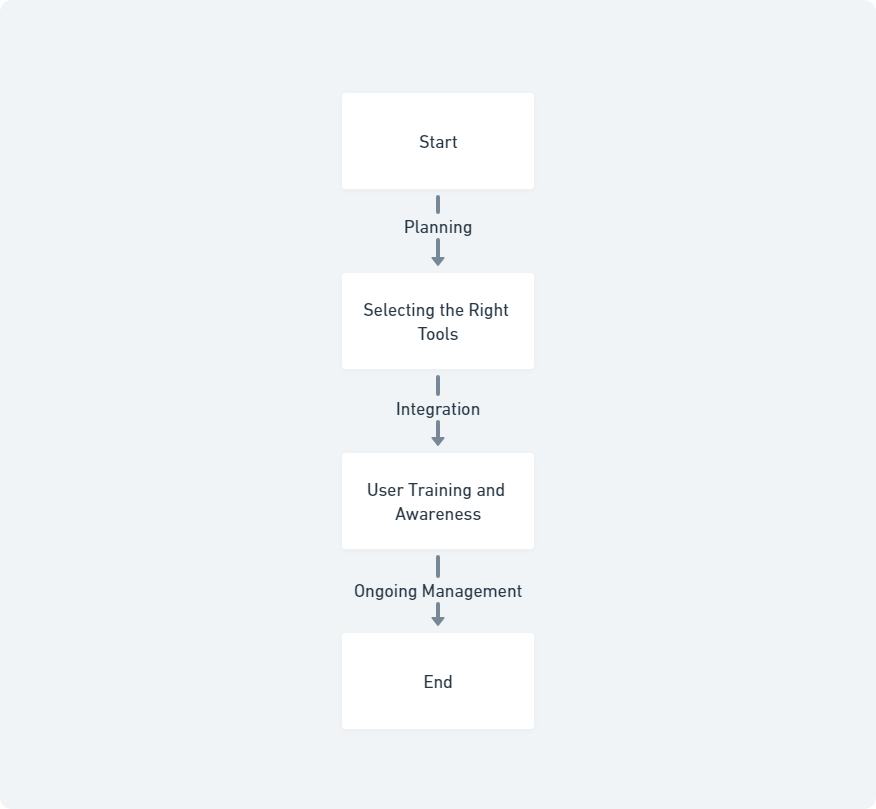
Implementing Identity and Access Management (IAM) effectively requires a structured approach. Here are the key steps to ensure successful IAM deployment:
- Planning: Start with a comprehensive assessment of your organisation’s current identity management processes and identify gaps. Define clear objectives and requirements for the IAM system, considering compliance with regulations such as the Privacy Act 1988 and the NDB scheme.
- Selecting the Right Tools: Choose IAM tools that align with your organisation’s needs. Consider factors such as scalability, integration capabilities, and specific features like SSO, MFA, and user provisioning. Vendors like Okta, Microsoft Azure AD, and SailPoint offer robust solutions that cater to diverse requirements.
- Integration: Seamlessly integrate the IAM system with existing IT infrastructure. Ensure compatibility with various applications, databases, and directories. This may involve configuring APIs and connectors to enable smooth communication between the IAM system and other components.
- User Training and Awareness: Educate employees on the importance of IAM and how to use the new system. Conduct training sessions and provide resources to help users adapt to changes, thereby ensuring higher adoption rates and compliance.
- Ongoing Management: Regularly review and update access policies to reflect organisational changes. Perform regular audits to detect and correct any discrepancies. Utilise monitoring tools to track user activities and detect potential security threats promptly.
Common IAM Challenges in Australia
Australian businesses often face several challenges in implementing Identity and Access Management (IAM) systems. One major issue is the integration with legacy systems. Many organisations have outdated IT infrastructures that are not easily compatible with modern IAM solutions, leading to complex and costly integration processes.
User adoption is another significant challenge. Employees may resist new IAM systems due to unfamiliarity or perceived complexity, which can hinder effective implementation. Ensuring user training and ongoing support is crucial to overcoming this barrier.
Compliance with regulatory requirements, such as the Privacy Act 1988 and the Notifiable Data Breaches (NDB) scheme, also poses challenges. Organisations must ensure their IAM systems align with these regulations to avoid legal repercussions and maintain data integrity.
Case studies have highlighted these challenges, such as the difficulty faced by a major Australian financial institution in integrating IAM with its legacy banking systems. Reports from cybersecurity firms underscore the need for comprehensive planning and user education to address these issues effectively.
| Challenge | Potential Solution |
|---|---|
| Legacy Systems Integration | Invest in middleware and APIs to bridge compatibility |
| User Adoption | Conduct thorough training and provide continuous support |
| Compliance Issues | Regularly review and update policies to meet regulations |
Addressing these common challenges through strategic planning, robust training programmes, and adherence to regulatory standards can significantly enhance the effectiveness of IAM implementations in Australian businesses.
Best Practices for IAM
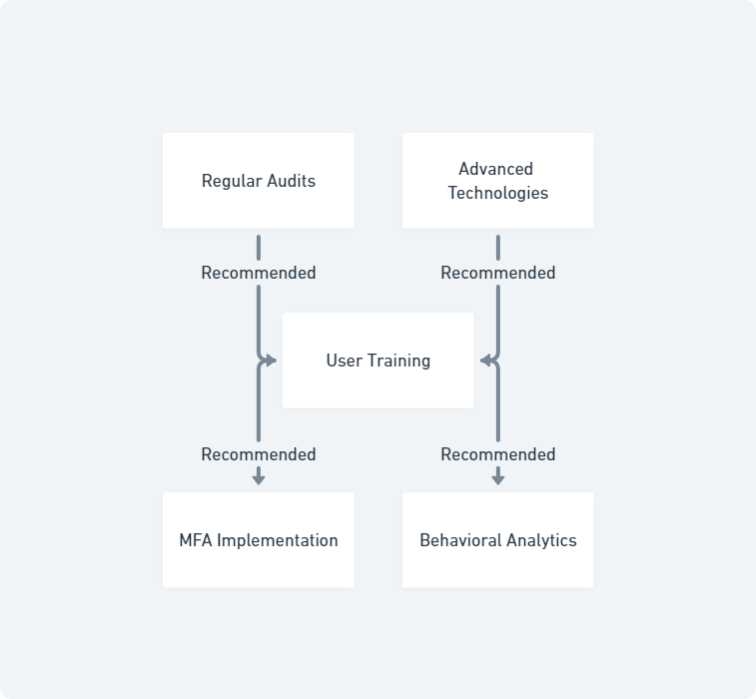
Maintaining an effective Identity and Access Management (IAM) system requires adhering to best practices that ensure security, compliance, and efficiency. Regular audits are essential to identify and rectify vulnerabilities. Conducting periodic reviews of user access rights helps to ensure that permissions are up-to-date and appropriate, mitigating the risk of unauthorised access.
User training is another critical component. Educating employees about the importance of IAM and how to use the system correctly can significantly enhance its effectiveness. Ongoing training sessions and resources should be provided to keep users informed about new features and security protocols.
Leveraging advanced technologies can further strengthen IAM systems. Implementing multi-factor authentication (MFA) and using behavioural analytics can help detect and prevent suspicious activities. Tools like Microsoft Azure AD and Okta offer robust features that support these advanced technologies.
Best practice guides from cybersecurity authorities, such as the Australian Cyber Security Centre (ACSC) and the National Institute of Standards and Technology (NIST), provide comprehensive advice on IAM strategies.
Following these guidelines can help organisations maintain a secure and compliant IAM system.
Future Trends in IAM

The landscape of Identity and Access Management (IAM) is evolving rapidly with several innovative trends emerging. AI-driven IAM is at the forefront, utilising machine learning to enhance security through predictive analytics and automated threat detection. This approach enables more precise and adaptive responses to potential breaches.
The zero trust security model is gaining traction, operating on the principle of “never trust, always verify.” This model ensures continuous verification of users and devices, significantly reducing the risk of unauthorised access.
Blockchain-based identity management is another promising trend. By leveraging blockchain’s decentralised nature, it offers enhanced security and privacy, ensuring that user identities are immutable and verifiable without relying on a central authority.
For detailed insights into these emerging IAM technologies, refer to whitepapers and articles from leading cybersecurity organisations and vendors, such as the Australian Cyber Security Centre (ACSC).
In summary, Identity and Access Management (IAM) is essential for maintaining the security and operational efficiency of Australian businesses. By implementing robust IAM strategies, organisations can protect sensitive data, comply with regulatory requirements, and streamline user access. Key elements such as single sign-on, multi-factor authentication, and access governance play vital roles in enhancing security. As cyber threats continue to evolve, adopting advanced IAM technologies and best practices becomes imperative. Businesses are encouraged to prioritise IAM to safeguard their digital assets and maintain a resilient security posture.
