
The exponential growth of digital interactions has fundamentally altered the security landscape for Australian organisations. A recent report by the Australian Cyber Security Centre (ACSC) revealed a 13% increase in cybercrime incidents reported in the last year alone, with many stemming from compromised user credentials . This alarming trend underscores the critical role of Identity and Access Management (IAM) in fortifying organisational defences.
IAM acts as the gatekeeper, meticulously verifying user identities and meticulously controlling access privileges to critical systems and data. Imagine a large office building: a robust IAM system functions like a secure keycard system, granting entry only to authorised individuals and restricting access based on their designated roles. Without a well-integrated IAM solution, organisations remain vulnerable to unauthorised access attempts, potentially leading to devastating data breaches and crippling financial losses.
Recognising the limitations of siloed security solutions, forward-thinking organisations are increasingly seeking to integrate IAM with their existing security infrastructure. This holistic approach fosters a unified security posture, ensuring consistent and comprehensive protection across all applications and data stores. However, integrating IAM seamlessly is not without its challenges. This article delves into the complexities of integrating IAM with existing security controls, explores the common pitfalls, and offers practical strategies to navigate the integration process successfully.
The Benefits of Integrated Security

Fragmenting security controls across disparate systems creates a blind spot for Australian organisations, leaving them susceptible to sophisticated cyberattacks. Integrating IAM with existing security tools fosters a more robust and unified security posture, offering a multitude of advantages.
One of the most significant benefits is the establishment of centralized access control. Imagine a single, intuitive interface for managing user access across all applications and data repositories. This eliminates the need for juggling multiple login credentials and simplifies permission assignments, minimising the risk of human error and unauthorised access. Furthermore, integrated IAM facilitates role-based access control (RBAC), dynamically granting or revoking access privileges based on a user’s designated role within the organisation. This granular control ensures that users only have access to the data and systems they require to perform their duties, effectively minimising the potential for data breaches.
Beyond access control, integrated security enhances overall visibility. A unified platform provides a comprehensive view of user activity across the organisation’s IT infrastructure. Security teams can readily identify suspicious behaviour patterns or anomalous access attempts, allowing for a swift and targeted response. This proactive approach strengthens an organisation’s ability to detect and mitigate potential threats before they escalate into major security incidents.
Streamlined user management is another key benefit. Integrated IAM eliminates the need for maintaining duplicate user accounts across various systems. This not only reduces administrative overhead for IT teams but also minimises the risk of orphaned accounts – inactive accounts that remain accessible and pose a security vulnerability. User provisioning and de-provisioning become streamlined, ensuring that access privileges are granted and revoked efficiently, reflecting changes in personnel or job roles.
The Australian Cyber Security Centre (ACSC) actively promotes integrated security as a cornerstone of cyber resilience. Their Essential Eight Strategies, a prescriptive framework for mitigating cyber threats, explicitly highlights the importance of multi-factor authentication and application control – functionalities often embedded within robust IAM solutions [https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/essential-eight]. By aligning with these best practices, organisations can leverage integrated IAM to not only enhance security but also demonstrate their commitment to regulatory compliance.
Key Benefits of Integrated Security
| Benefit | Description |
|---|---|
| Centralized Access Control | Manage user access across all systems from a single platform. |
| Role-Based Access Control (RBAC) | Grant access privileges based on a user's designated role. |
| Enhanced Visibility | Gain a comprehensive view of user activity across the IT infrastructure. |
| Streamlined User Management | Efficiently provision and de-provision user accounts. |
| Regulatory Compliance | Align with best practices outlined by the ACSC Essential Eight Strategies. |
Challenges of Integrating IAM

The journey towards a unified security posture through IAM integration is not without its roadblocks. Organisations striving to implement a new IAM solution often encounter a multitude of challenges stemming from pre-existing IT infrastructure and internal workflows.
A significant hurdle lies in the inherent heterogeneity of security environments. Many organisations have accumulated a patchwork of security tools and systems over time, often from different vendors and with varying levels of compatibility. Integrating a new IAM solution seamlessly into this complex ecosystem can be a daunting task. For instance, a financial services company might utilise a legacy on-premises access control system alongside cloud-based security tools. Reconciling these disparate solutions with the new IAM platform can require extensive configuration and customisation efforts.
Data synchronization presents another significant challenge. Ensuring consistent and accurate user identity and access information across all platforms integrated with IAM is paramount. Inconsistencies can lead to security gaps and user access disruptions. Imagine a scenario where a retail organisation acquires a new e-commerce platform. Integrating the IAM system with the new platform requires meticulously synchronizing user data, including usernames, roles, and access privileges, across both systems. Failure to achieve this synchronization could leave customer data vulnerable or hinder employee productivity. A recent study by IBM revealed that data inconsistencies cost Australian businesses an average of $6.4 million annually.
Process integration also presents a hurdle. Organisations have established workflows and procedures for user provisioning, access management, and security incident response. Implementing a new IAM solution necessitates aligning these existing processes with the functionalities and workflows offered by the platform. For instance, a healthcare provider might have a well-defined process for granting temporary access to visiting specialists. Integrating IAM requires adapting this process to leverage the user provisioning and access control features within the new platform. Resistance to change management from internal stakeholders can further complicate this integration process.
Securing user adoption and fostering a culture of security awareness are crucial for successful IAM integration. A new IAM system, no matter how sophisticated, cannot function effectively if users circumvent its controls or struggle to navigate its interface. Comprehensive user training on the new platform’s functionalities and security best practices is essential. For example, a manufacturing company implementing IAM might encounter initial user resistance to multi-factor authentication protocols. Providing clear explanations regarding the enhanced security benefits and conducting user training sessions can help overcome these hurdles.
Finally, navigating the ever-evolving landscape of data privacy regulations presents a challenge. Organisations must ensure that their IAM implementation adheres to relevant legislation, such as the Australian Privacy Act (1988) and the Notifiable Data Breaches (NDB) scheme. For instance, the NDB scheme mandates reporting of data breaches involving personal information. A well-configured IAM system with robust audit trails can facilitate compliance with such regulations by providing a clear record of user activity and access attempts.
By acknowledging these challenges and implementing well-defined strategies, organisations can navigate the IAM integration process successfully. The following section explores practical solutions to overcome these hurdles and achieve a robust and unified security posture.
Strategies for Successful Integration
Successfully integrating IAM with existing security controls requires a strategic approach that addresses the challenges outlined in the previous section. Here are practical strategies to navigate the integration process:
1. Standardization
Heterogeneity within the security landscape can be a significant roadblock. Organisations can mitigate this challenge by establishing consistent security configurations across all systems. This might involve standardizing on specific protocols for authentication and authorization, or adopting a uniform approach to user provisioning. For instance, a telecommunications company can mandate the use of SAML (Security Assertion Markup Language) for single sign-on across all cloud-based applications integrated with the IAM system. Standardization simplifies the integration process and minimizes the need for custom configurations for each individual system.
2. Phased Implementation
A big-bang approach to IAM integration can be disruptive and overwhelm internal stakeholders. A more effective strategy is a phased implementation, prioritizing critical systems and user groups first. This allows for a more controlled rollout, enabling IT teams to identify and troubleshoot any integration issues early on. For example, a logistics company might prioritize integrating the IAM system with their core warehouse management system and then gradually extend access control to other less critical applications. This phased approach minimizes disruption to daily operations while ensuring the most essential systems benefit from enhanced security measures.
3. Data Governance Framework
Data synchronization is paramount for successful IAM integration. Establishing a clear data governance framework ensures the accuracy and consistency of user identity and access information across all integrated platforms. This framework should define roles and responsibilities for data ownership, quality control procedures, and data lifecycle management. For instance, a government agency can designate a specific team within the IT department to oversee data quality within the IAM system. Regular data audits and reconciliation processes should be implemented to identify and rectify any discrepancies.
4. User-Centric Approach
User adoption is critical for maximizing the value of IAM. Organisations must prioritize user experience by ensuring the IAM system is intuitive and user-friendly. Investing in comprehensive user training on the new platform’s functionalities and security best practices is essential. Furthermore, ongoing communication and support channels should be established to address user concerns and encourage feedback. For example, a manufacturing company can develop user guides and video tutorials specifically tailored to different user roles within the organization. By prioritizing user experience and fostering a culture of security awareness, organizations can encourage user adoption and maximize the effectiveness of their IAM solution.
5. Compliance Mapping
Navigating the complexities of data privacy regulations necessitates a proactive approach. Organisations should conduct a thorough compliance mapping exercise to identify any potential gaps between their existing security posture and relevant data privacy legislation such as the Australian Privacy Act (1988) and the NDB scheme. The IAM implementation should then be aligned to address these gaps. For instance, an educational institution might leverage the robust audit trails generated by the IAM system to demonstrate compliance with the NDB scheme and facilitate timely reporting of any data breaches involving student information. By aligning IAM with relevant regulations, organisations can build trust with stakeholders and minimize the risk of regulatory non-compliance.
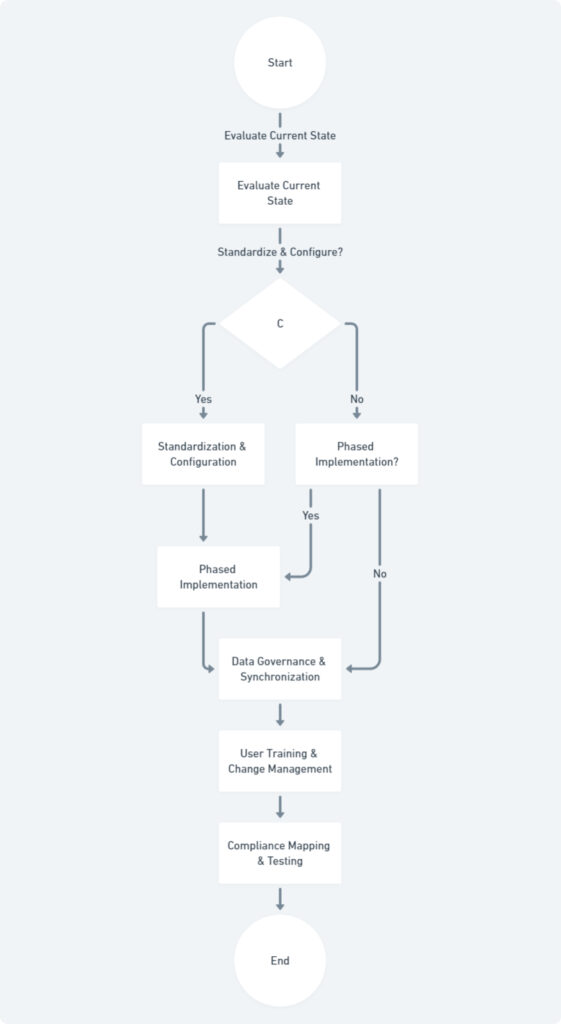
Stages of IAM Implementation: A Comprehensive Overview
- Planning and Assessment: This stage involves evaluating existing security infrastructure, user access controls, and data management practices.
- Standardization and Configuration: This stage focuses on establishing consistent security configurations across all systems to be integrated with IAM.
- Phased Implementation: This stage outlines the gradual rollout of IAM, prioritizing critical systems and user groups first.
- Data Governance and Synchronization: This stage defines procedures for ensuring accurate and consistent user data across all integrated platforms.
- User Training and Change Management: This stage includes user training programs and communication strategies to promote user adoption of the new IAM system.
- Compliance Mapping and Testing: This stage involves aligning IAM implementation with relevant data privacy regulations and conducting thorough testing to ensure functionality and adherence to compliance requirements.
By implementing these strategies and adopting a well-defined integration process, organisations can navigate the challenges of integrating IAM and achieve a robust and unified security posture.
In conclusion, integrating IAM with existing security controls offers significant advantages, fostering a centralized approach to access management, enhancing visibility and streamlining user administration. However, navigating the complexities of heterogeneous environments, data synchronization and process integration requires a strategic approach. By implementing well-defined strategies and embracing a user-centric mindset, organisations can successfully overcome these challenges and unlock the full potential of IAM. Looking ahead, the evolving threat landscape and the emergence of new technologies like cloud-native security solutions will necessitate continuous adaptation and innovation in IAM integration strategies.
