
Navigating the Digital Landscape with IAM
The Australian business landscape is undergoing a digital metamorphosis, with a surge of 35% in cloud adoption reported in 2023 alone. While this digital transformation unlocks new opportunities, it also exposes businesses to heightened security vulnerabilities. In fact, a recent report by the Australian Cyber Security Centre (ACSC) revealed that cybercrime cost Australian businesses an estimated $39 billion in 2022. These statistics paint a stark picture: robust security measures are no longer a luxury, but a necessity.
One of the most critical aspects of cybersecurity involves managing user identities and access permissions. Imagine a scenario where a disgruntled ex-employee retains access to confidential financial data, highlighting the potential consequences of inadequate access control. This is where Identity and Access Management (IAM) steps in, offering a comprehensive approach to streamlining security and regaining control in the digital realm.
However, despite its evident benefits, confusion often surrounds IAM implementation, particularly for Australian businesses navigating the complexities of diverse security solutions. This guide aims to demystify IAM, providing a clear and accessible explanation for organisations of all sizes. By understanding the core principles and practical steps involved, Australian businesses can embrace the power of IAM, navigate the digital landscape with confidence, and safeguard their valuable assets.
What is IAM?
Identity and Access Management (IAM) is the cornerstone of robust cybersecurity, serving as the orchestrator of who can access what, and when, within your organisation. It encompasses two core functions:
- Identity Management: This involves establishing and managing the digital identities of all users within your organisation, including employees, contractors, and external partners. This includes creating user accounts, assigning usernames and passwords, and maintaining accurate user information.
- Access Management: This crucial function focuses on controlling access to critical resources and data based on pre-defined permissions. Imagine granting specific employees access to specific applications or documents, ensuring only authorised personnel can view or modify sensitive information. This granular control is fundamental to preventing unauthorised access and potential data breaches.
Implementing IAM offers a multitude of benefits for Australian businesses:
- Enhanced Security & Compliance: IAM safeguards sensitive data by ensuring only authorised individuals have access. This reduces the risk of data breaches, which can lead to significant financial losses and reputational damage, and helps organisations comply with relevant Australian regulations, such as the Privacy Act 1988 and the Notifiable Data Breaches (NDB) scheme.
- Improved Manageability & Control: IAM streamlines user management and simplifies access control processes. This reduces the administrative burden on IT teams and empowers businesses to manage user access efficiently and effectively.
- Increased Productivity & Efficiency: By eliminating the need for manual access provisioning and revoking, IAM boosts productivity for both IT teams and end-users. Additionally, clear and defined access control minimizes confusion and ensures users have the necessary access to perform their tasks efficiently.
The importance of IAM in the Australian context cannot be overstated. The ACSC reports a 13% increase in cybercrime incidents reported in 2023 compared to the previous year, highlighting the growing need for robust security solutions. Additionally, the recent Optus data breach, which compromised the personal information of millions of Australians, underscores the critical role of IAM in safeguarding sensitive data.
By understanding IAM and its functionalities, Australian businesses can take a proactive approach to cybersecurity and navigate the digital landscape with confidence.
Resources:
- Australian Cyber Security Centre (ACSC) IAM guidance: https://www.cyber.gov.au/
- Australian Information Security Manual (ISM): https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/ism
Key Components of IAM: The Building Blocks of Secure Access
Identity and Access Management (IAM) hinges on three crucial pillars that work in tandem to safeguard your organization’s data and resources:
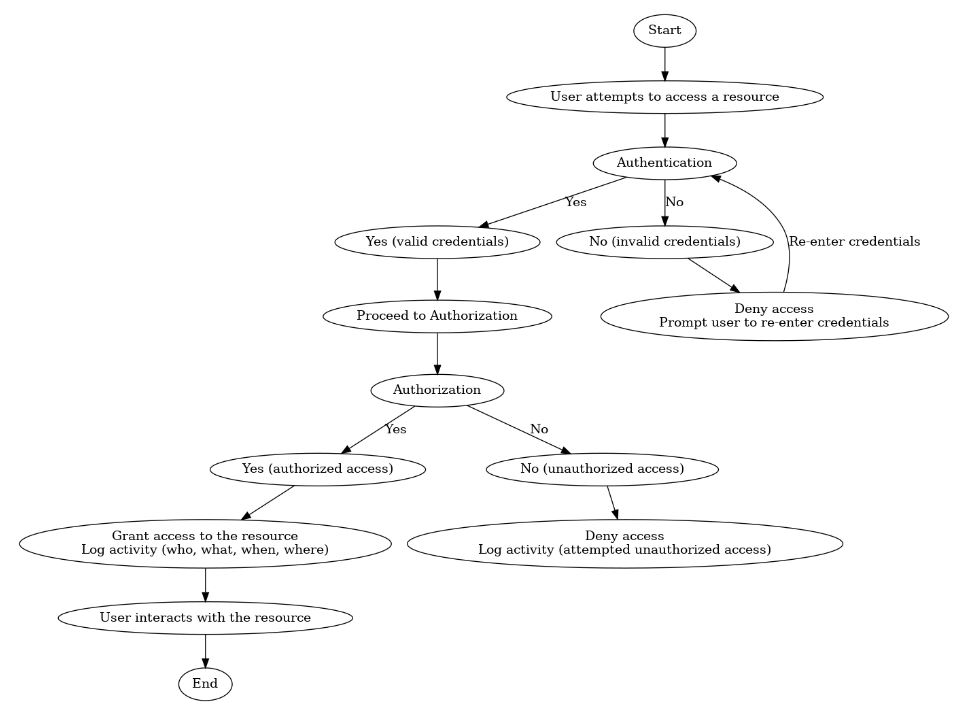
1. Authentication

Imagine a door with a complex lock; authentication is like the key that verifies the legitimacy of a user attempting to enter. It ensures that only authorized individuals gain access to protected systems and information. Common authentication methods include:
- Passwords: The traditional method, but increasingly vulnerable due to password fatigue and breaches.
- Multi-factor authentication (MFA): Adds an extra layer of security by requiring additional verification factors, such as a one-time code sent to a mobile device, alongside a username and password.
2. Authorization

This pillar determines the “level of access” granted to a user after their identity is verified through authentication. It’s like assigning a specific key that unlocks only specific doors within the building. Here’s where access control models come into play:
- Role-based access control (RBAC): Assigns permissions based on user roles (e.g., finance team members have access to financial data, but not marketing materials). This simplifies management by grouping similar access needs.
3. Auditing

Keeping a watchful eye is crucial. Auditing involves monitoring and logging user activity within systems, creating a record of who accessed what, when, and from where. This serves two primary purposes:
- Security: By analyzing audit trails, organizations can detect suspicious activity, identify potential breaches, and take corrective action.
- Compliance: Audit logs provide evidence that organizations are adhering to relevant data security regulations and can be instrumental in demonstrating compliance efforts.
Visualizing the Interaction:
Resources:
- National Institute of Standards and Technology (NIST) IAM framework: https://www.nist.gov/identity-access-management
By understanding these key components and their interplay, Australian businesses can leverage IAM to build a robust security framework that protects valuable data and fosters a secure digital environment.
Implementing IAM in Your Australian Business
Taking control of your organization’s digital security landscape requires a structured approach to implementing IAM. Here’s a roadmap to guide Australian businesses through the process:
1. Planning & Assessment
- Identify critical resources: This forms the foundation of your strategy. Pinpoint the most sensitive data and systems within your organization, such as customer records, financial data, and intellectual property.
- Analyze access needs: Understand the various user roles and their legitimate access requirements for each identified resource. This helps in establishing a clear picture of who needs access to what.
- Define security policies: Establish clear and well-defined security policies that govern user access, password management, and data handling. Ensure these policies align with relevant Australian regulations, such as the Privacy Act 1988 and the Notifiable Data Breaches (NDB) scheme.
2. Selection & Implementation
- Choose an appropriate IAM solution: Explore various IAM solutions available in the market, considering factors like your business size, budget, and specific security needs. Seek guidance from IT security professionals if needed.
- Implementation: Once chosen, carefully implement the selected IAM solution, following the vendor’s instructions and best practices. This may involve integrating the solution with existing IT infrastructure and migrating user data securely.
3. Deployment & Configuration
- Configure access controls: This is where the “who, what, where, when, and why” of access gets defined. Utilize the access control models (e.g., RBAC) discussed earlier to assign appropriate access permissions to users based on their roles and needs.
- Enable multi-factor authentication (MFA): This adds an essential layer of security by requiring an additional verification step beyond just a username and password.
4. Training & Awareness
- Educate employees: Empower your workforce by conducting training sessions on IAM policies, user access procedures, and best practices for secure online behaviour. Foster a culture of cybersecurity consciousness within your organisation.
5. Ongoing Monitoring & Maintenance
- Regularly review user activity: Monitor audit logs to identify any suspicious or unauthorized access attempts. Swiftly examine and respond to any potential security infringements.
- Update access permissions: Periodically review user access needs and adjust permissions accordingly, ensuring they remain aligned with current roles and responsibilities.
- Stay informed: Keep abreast of the evolving cyber security landscape and update your IAM strategy and solutions as needed to address emerging threats and vulnerabilities.
6. Australian-specific Considerations
- Leverage the ACSC Essential Eight Strategies to strengthen your overall cybersecurity posture.
- Familiarize yourself with the resources and guidance provided by the Office of the Australian Information Commissioner (OAIC) regarding data privacy regulations.
By following these steps and adhering to best practices, Australian businesses can effectively implement IAM and navigate the digital landscape with greater confidence, safeguarding their valuable data and assets. Remember, IAM is an ongoing process, requiring continuous monitoring, adaptation, and employee engagement to ensure long-term security success.
Navigating the evolving cybersecurity landscape requires proactive measures. Robust Identity and Access Management (IAM) empowers Australian businesses to safeguard sensitive data, bolster trust, and maintain compliance. This guide has highlighted IAM’s importance, explored common threats, and provided actionable steps to strengthen your IAM posture.
Remember, a comprehensive IAM strategy is an investment in your organization’s future, protecting valuable assets, reputation, and stakeholder trust. We encourage you to explore the provided resources and seek professional guidance when needed. The ACSC and other industry bodies offer extensive support to assist your cybersecurity journey.
